Intel® Enhanced Privacy ID Ecosystem
Everything you need to verify your target devices while safeguarding privacy
The Intel® EPID ecosystem is composed of Intel® EPID keys, devices, and service providers. Keys are provisioned to devices either at manufacture time, or at the time a device joins a trusted group. Verification ensures that the device is a Member of a trusted device family before the device receives a service.
Intel EPID Keys
Devices need to be provisioned with keys from an Issuer to use the verification service.
Anonymous Devices
Devices have keys and software that allow them to prove their identity anonymously.
Service Providers
Service providers provide services to trusted devices.
Learn about Service Providers
As a service provider, you can use Intel's verification service, or you can create your own Verifier with the Intel® EPID SDK.
In the Intel® EPID scheme, you need a Verifier to prove that a device is a valid Member of a trusted group. In real-world use cases, Members don't request verification directly from the Verifier, because the Member already trusts itself. Instead, a service provider acts as an intermediary between the Member and the Verifier. The service provider requires a Member device to be verified before the Member device can receive a service.
The Intel® EPID SDK provides Verifier APIs to help you implement your own Verifier. Intel also provides a verification service, so that if you don’t want to implement your own Verifier, you can send Intel® EPID signatures to the verification service. The service will respond indicating that the signature is either valid or invalid.
Learn about Devices
Devices that comply to the Intel® EPID standard contain cryptographic keys issued by Intel, and they run software based on the Member component of the Intel® EPID SDK.
Prerequisites
- Secure storage for a key of 144 bytes.
- Some form of network connectivity to send and receive messages for verification.
- Optionally, Members may have cryptographic acceleration hardware for elliptic curves.
Developing Intel® EPID Software for Your Device
After you download the SDK, you can build the SDK and run samples with test data (also called sample Issuer material), which includes sample key material and revocation lists.
Download the SDK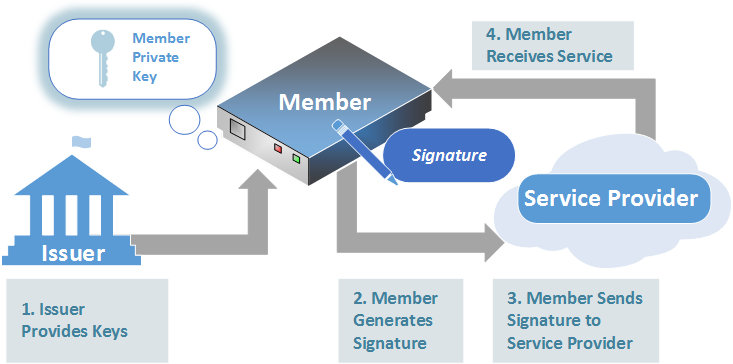
Learn about Keys
You need keys from an Issuer to provision your devices in order to use a verification service.
An Issuer is responsible for managing group membership. Issuer functionality is not included in the SDK.
To use the Intel Key Generation Facility (iKGF) as an Issuer, contact info@digital-cp.com to get started.Contact the Intel Key Generation Facility
For Intel® EPID keys, you could implement your own Issuer, but at this time, the Intel Key Generation Facility (iKGF) is the only available Issuer.
Provisioning Devices with Intel® EPID Key Material
Group membership is managed by an Issuer. Issuers provide keys for Member devices through bulk provisioning. At this time, the Intel Key Generation Facility (iKGF) is the only available Issuer, so you will need to work with iKGF to obtain genuine key material and revocation lists. (iKGF is a wholly owned subsidiary of Intel, and is an independent company.)
Then you will need to provision each device with genuine key material from the Issuer.
- Contact iKGF by emailing info@digital-cp.com to get started. Then iKGF will generate cryptographic key material for each device in your trusted device family.
- iKGF provides a group public key, Member private keys, and revocation lists for each group.
- Provision devices with Member private keys by fusing a Member private key into each device.
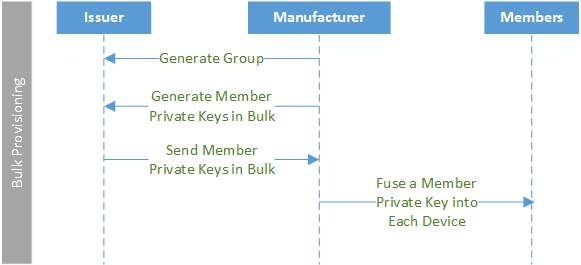
How does an Issuer Provide Keys and Manage Groups?
An Issuer creates and manages groups.
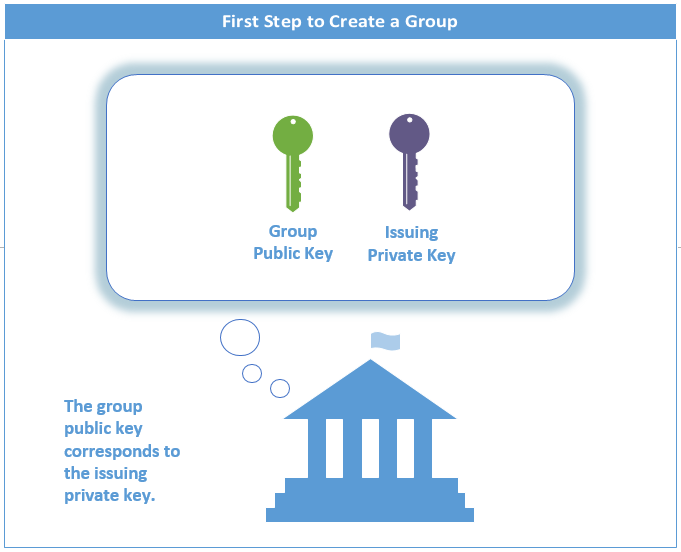
To create a group, first an Issuer generates one issuing private key and one group certificate for each group. The group certificate contains the group public key.
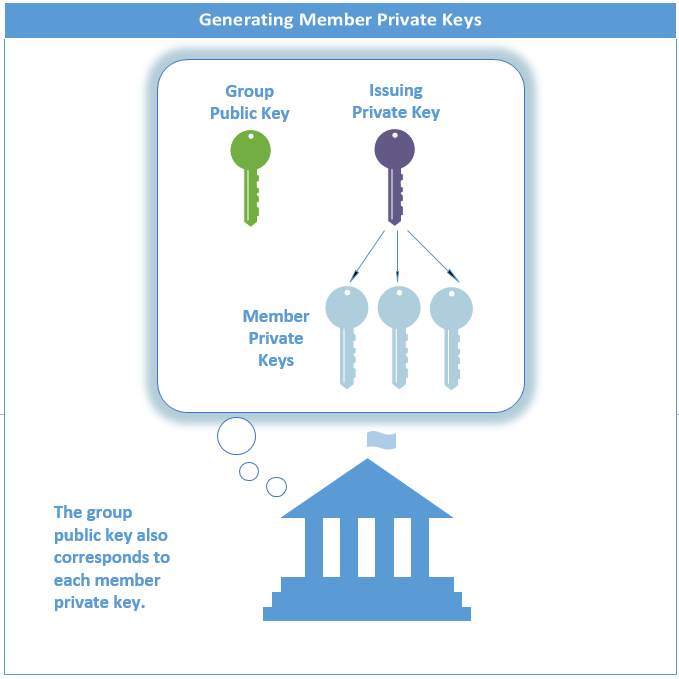
Next, the Issuer creates group members by generating unique Intel® EPID Member private keys through bulk provisioning. Member private keys are created from the issuing private key for the group. After the group is created, the Issuer uses the join protocol to manage subsequent requests from prospective members to join existing groups.
A single group public key corresponds to each Member private key in the group.
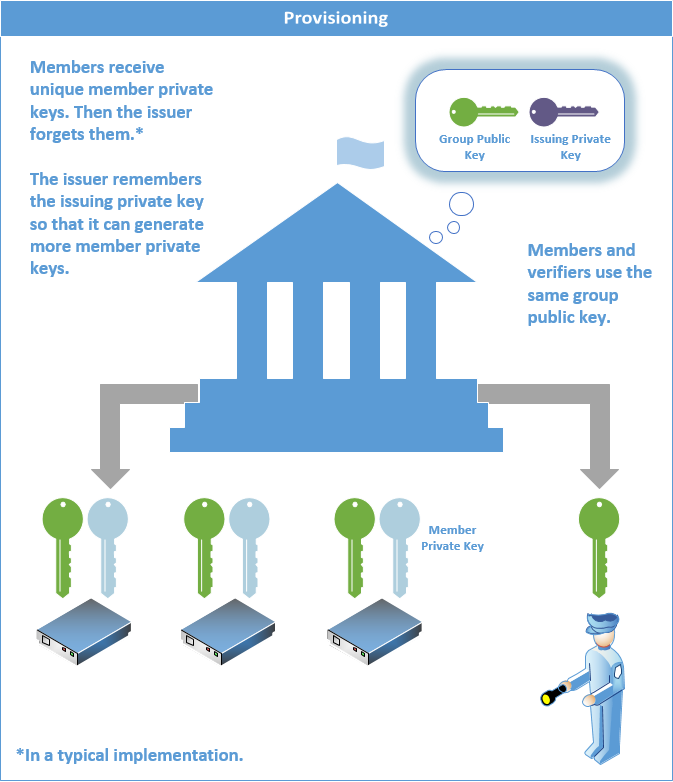
Each member receives a Member private key. The Issuer remembers the issuing private key so that it can generate more Member private keys if more devices join the group.
The Issuer also creates and maintains revocation lists. These lists of Members no longer in good standing allow Members to be dropped from a group.
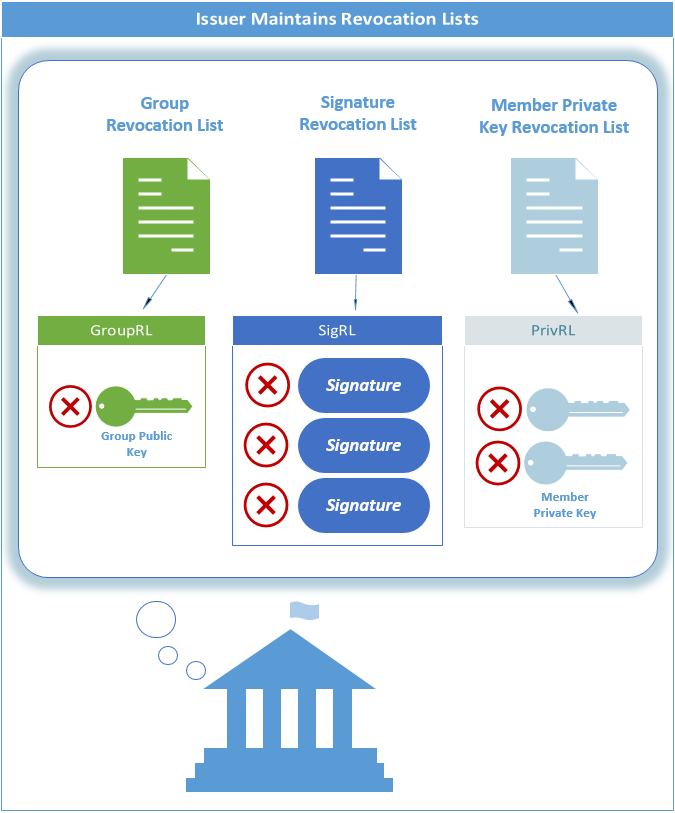
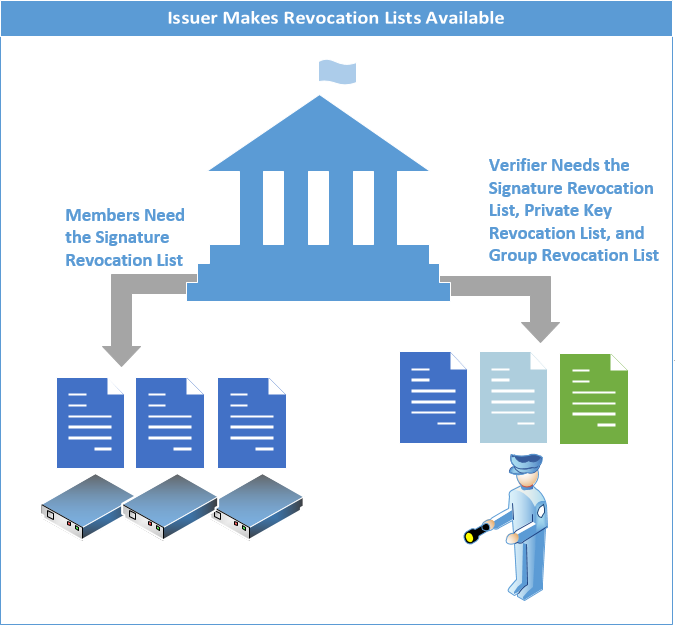
The Issuer makes group public keys and revocation lists available to Verifiers. It also makes the signature revocation list available to Members.
Members need the signature revocation list to sign messages, while Verifiers need all revocation lists for verification.
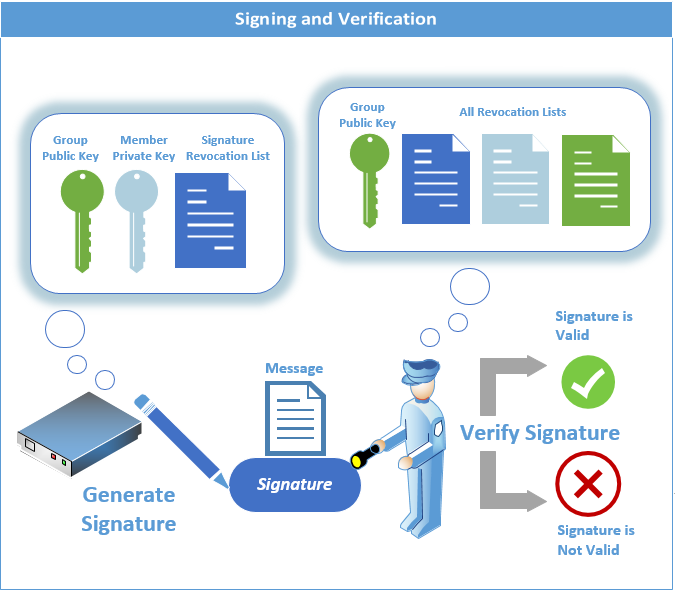
Finally, each Member uses its Intel® EPID Member private key to digitally sign a message. The resulting signature is called an Intel® EPID signature.
The Verifier uses the group public key to verify the correctness of an Intel® EPID signature, i.e., to verify that the signature was indeed created by a Member with a valid Intel® EPID Member private key.
However, the Intel® EPID signature does not convey any information about which unique private key was used to create the signature. Furthermore, two signatures from the same Member are not similar enough that the Verifier can tell that they came from the same Member. In other words, the Member's signature cannot be recognized based on its similarity to another signature.
How Do the Devices, Verifier, and Service Provider Interact with an Issuer?
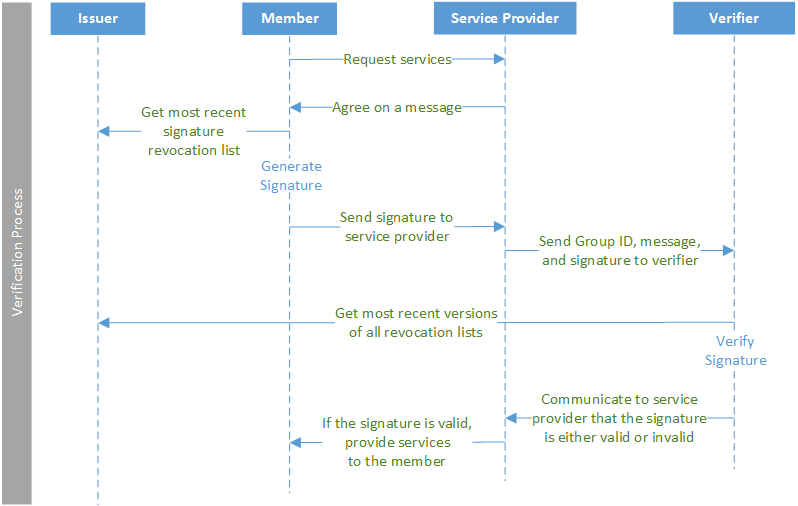
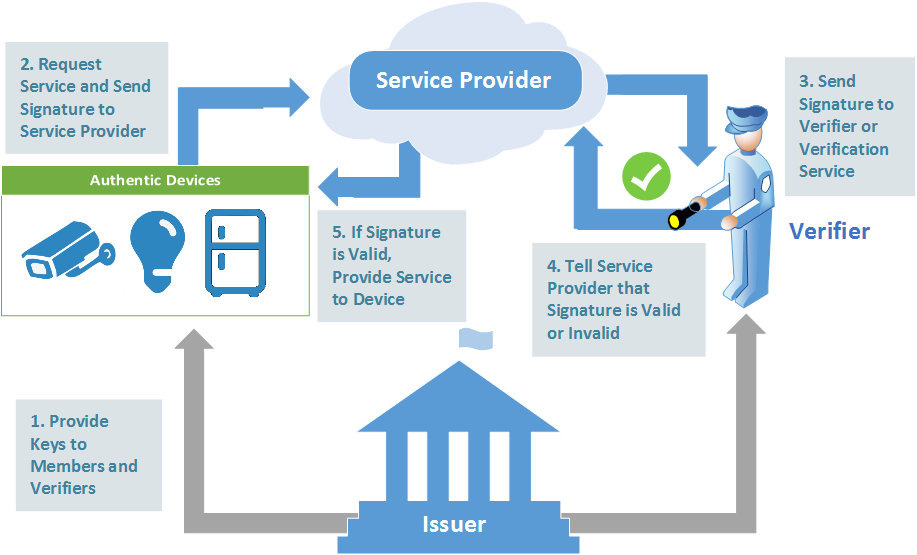
A Member, Verifier, and service provider might have the following interaction with an Issuer:
- The Member requests a service from the service provider. The service provider requires verification. The Member device and the service provider agree on the message that the Member will use to generate a signature.
- The Member gets the most recent signature revocation list from the Issuer.
- The Member signs the message using the agreed-upon message, the Member private key, and the most recent signature revocation list.
- The Member sends the signed message to the service provider.
- The service provider sends the group ID, message, and signature to the Verifier.
- Using the most recent revocation lists from the Issuer, the Verifier (or verification service) validates the signature. It indicates to the service provider if the signature is valid or invalid.
- If the signature is valid, the service provider allows the Member device to receive the service.